24×7 MANAGED SECURITY SERVICES
24×7 Monitoring. SIEM and SOC Building. Log Management Services
24×7 Managed Security Services
 24×7 Perimeter Defense
24×7 Perimeter Defense
24×7 Monitoring is essential to maintaining effective Cybersecurity as Hackers may strike when you least expect it. Establishing ‘tripwires’ alerts you from the inception of a Hacker Event.
Early detection of complex attacks facilitates early disruption and protects the organization from the most serious intrusions. Perimeter defense provides constant monitoring of Threats and possible Attack Vectors.
 24×7 Managed Detection and Response
24×7 Managed Detection and Response
Cybots AI-driven MDR incorporates Automation and Integration to provide you with best-in-class end-point solutions for your cyber defense. Early detection facilitates early disruption and containment.
Automation facilitates low touch, high-efficiency and less human error.
Integration facilitates, context, streamlined workflow, and reduced system count and expense.
 24×7 Managed SOC Services
24×7 Managed SOC Services
Our engineers have vast experience in SOC Build, Operation and Training.
We are able to provide a flexible array of operation management levels from Fully-Managed to Hybrid-Managed services to fit our clients’ operational requirements. This eliminates the need for the client to maintain staff levels overnight.
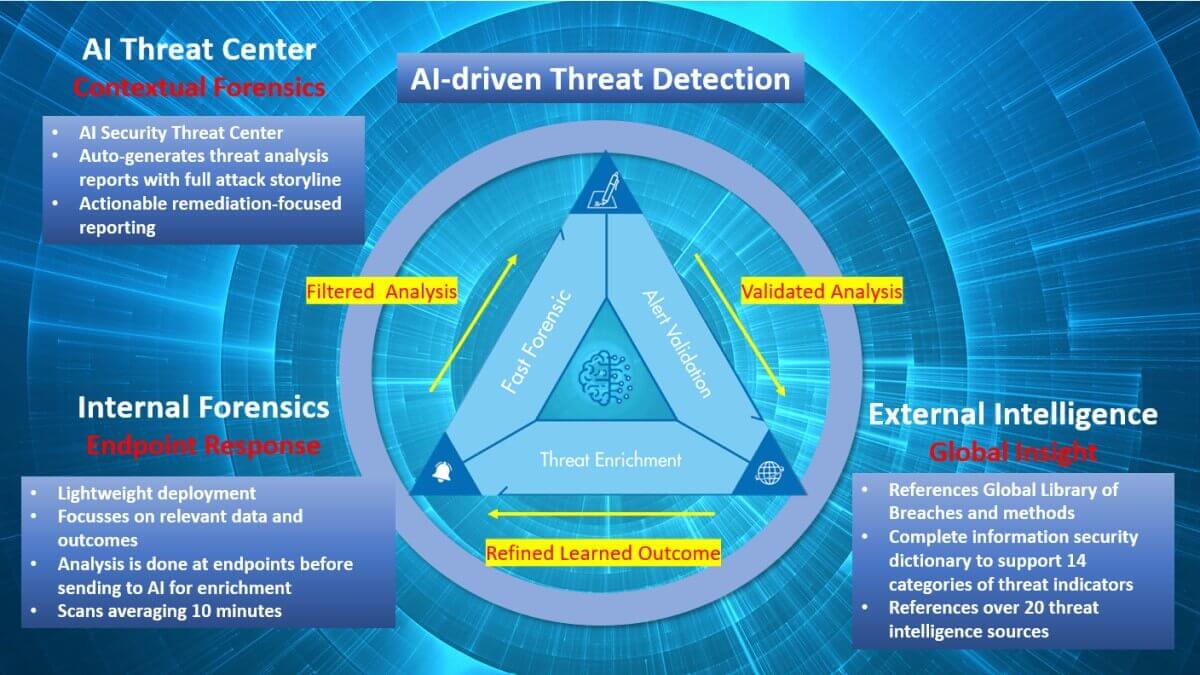
- Costs to ownership of a SOC.
- Maintaining trained staff levels to effectively operate a SOC.
- Operating a SOC on a 24×7 basis to cover monitoring gaps that a hacker might exploit.
- Addressing new threats that require constant updating.
We assess all security measures for your organization. We analyse security systems, study potential breaches, and supervise the implementation of solutions. We are able to address your security needs relating to People, Processes and Technology.